About This Episode
Podcast Episode 5
August 6, 2024 - 42 mins
IT support is tricky for most businesses, especially for those not in the IT business. Thus, IT is a cost of doing business and a high cost at that. High costs drive down profits. Less profit makes it harder for businesses to invest in the products or services that they’re making and selling. Retaining IT staff is even more difficult. This is due to the extremely low unemployment rate and the higher-than-average annual salary. These two factors almost guarantee that IT staff hired by non-IT businesses will eventually get a better offer some place else. To mitigate the problem with IT staff, businesses have turned to outsourcing to managed service providers or external service providers. By doing so businesses are giving up the information necessary to make well-informed choices, instead choosing to trust the IT service providers they’re buying from. This asymmetry of information creates a market phenomenon called a market for lemons. A market for lemons phenomenon exists when sellers hold more knowledge than buyers. Because buyers are price-sensitive and are only willing to pay a certain price the market becomes distorted such that high-quality sellers are gobbled up quickly and the market is left with lemons. In sum, the market for lemons works to drive quality out of the market.
Today’s guest is Andy Paul. Andy is an engineer, data privacy professional and a Certified CMMC Assessor from Gray Analytics with more than 15 years of experience helping firms design, implement and secure everything from globally spanning networks to small boutique and highly specified and regulated networks. During our conversation, we discuss the current situation in the IT services market, the market for lemons phenomenon, how the CMMC ecosystem is setup to alleviate the problems that markets for lemons introduce, and how you can outsource confidently.
Resources:
- George Akerlof – The Quarterly Journal of Economics, Vol. 84, No. 3 (Aug. 1970), pp. 488-500
- Cyber AB Marketplace
The core factors that drive creation of a market for lemons:
- Asymmetry of information: sellers hold more information
- Perverse incentive: passing off low quality products as high-quality products
- No credible discourse technology: there’s no way to prove quality
- Wide range of seller qualities drives the average seller quality low
- Lack of effective public quality assurances: no warranties or regulations
A simplified example of a market for lemons:
CMMC Registered Provider Organizations provide:
- Buyers with the knowledge to evaluate external service providers and products.
- Businesses with the ability to scope, design, correctly configure, and properly utilize services procured.
- Representation and guidance throughout the CMMC process.
- Reduced learning curve, greater efficiency of design, reduction in superfluous product purchases.
- Higher assessment success rates.
Red flags when outsourcing:
- Managed Service Providers
- Inability to provide a shared or customer responsibility matrix.
- Inability to provide or identify baseline configurations used.
- Mixing toolsets and configurations across CMMC and non-CMMC clients.
- Unwillingness to participate in an assessment.
- Over-reliance on other certification (i.e., SOC2 or ISO) that do not have reciprocity.
- External Service Providers
- Lack of FedRAMP Moderate or higher authorization or equivalency.
- Support is provided by US and Non-US Persons.
- Inability to identify controls they address as mapped to NIST SP 800-171.

Get the latest episodes on your favorite streaming platform.
Podcast use is subject to Kratos Terms.
Get email alerts on the latest episodes
Episode Transcript
Cole French:
Are you looking to hire solid IT folks, but find yourself priced out? Do you turn to service providers only to find you can’t seem to really figure out exactly what you’re paying for? Believe it or not, there’s a market phenomenon at play in the IT services market. Tune in as we discuss this phenomenon, the market for lemons. We’ll dive into how it plays out in the cybersecurity services market, how the CMMC ecosystem is set up to alleviate the problem, and how you can come out ahead and maximize your return on investment in IT and cybersecurity services.
Welcome to the Cyber Compliance and Beyond podcast, a Kratos podcast that brings clarity to compliance, helping you leverage compliance as a tool to drive your business’s ability to compete in any market. I’m your host, Cole French. Kratos is a leading cybersecurity compliance advisory and assessment organization providing services to both government and commercial clients across varying sectors, including defense, space, satellite, financial services, and healthcare. Now let’s get to today’s episode and help you move cybersecurity forward.
The cost of IT services is at an all-time high. For most organizations, IT is just that; a cost. IT doesn’t make or sell the product, nor do they provide a service that brings in a profit. IT services are like cars. They’re essential, but they’re expensive and their value is difficult to quantify.
The rising cost of IT services, combined with specialization, have pushed most organizations to outsource their IT services. The cost of in-house IT staff is simply too high, and there’s far too much turnover for stability. Outsourcing has helped businesses mitigate some of the cost. The price of this mitigation, however, is that outsourcing creates an asymmetry of information.
As we’ll discuss on today’s episode, this asymmetry of information where the sellers, or IT service providers, hold more information than the buyers, or businesses, creates the conditions for a market for lemons. In simple terms, a market for lemons exists when the conditions of the market work to drive quality out of the market.
On today’s episode, we’ll discuss the market for lemons and how the CMMC ecosystem is set up to alleviate this asymmetry of information, which is at the core of the market for lemons phenomenon. We’ll also discuss how the ecosystem is configured and how organizations can leverage the CMMC framework to successfully outsource their IT services.
Now, joining us for today’s conversation is Andy Paul. Andy is an engineer, data privacy professional and certified CMMC assessor from Gray Analytics, with more than 15 years of experience helping firms design, implement and secure everything from globally-spanning networks, to small boutique and highly-specified and regulated networks. We hope you enjoy this episode.
Andy, thank you for taking the time to join us today on the Cyber Compliance and Beyond podcast.
Andy Paul:
Hey, thanks, Cole. It’s a pleasure to be here.
Cole French:
So we’re going to talk today a little bit about what organizations face, when it comes to IT services in general and cybersecurity services in particular. So Andy, would you mind getting us started by telling us just a little bit about the predicament that businesses face when it comes to IT services?
Andy Paul:
Yeah, absolutely, I’d love to. So there’s an interesting market dynamic that’s formed over the past couple of decades, really, inside of the IT space. And it’s a market dynamic that’s based in a couple of recurring systemic problems that are out there. Well, first is this fact that in almost all businesses, IT staff are a burden. So IT staff don’t manufacture a widget, they’re not providing a service. They’re not selling a service. They don’t actually add revenue to my business. They don’t bring in additional revenue. They’re really just a drain. They hit my bottom line. We know that they’re necessary services, but they don’t help me generate revenue or create profit from my company. It’s like having cars or some of these side of expenses for my company. I don’t get a direct investment return. Making it really hard to calculate a return on investment for the amount of money I’m spending on my IT staff. And then the more money I spend on my IT staff, it just hits as a cost, right? I just want to lower my overall profit margins.
You can take that fact that sits there, and you combine it with the fact that IT services have historically had really low unemployment rates. Recently, it was reported as low as 1.3% as the average unemployment rate. This has come up a little bit in the just very recent terms. In the last couple of months, there’s been a slight uptick in it, but in general, IT services has one of the lowest unemployment rates that’s out there. And the average salary for these people, because of that low unemployment, there’s not a lot of workers in the pool to draw from, it’s more than double the average small business salary. So according to the 2021 US Census data, the average salary of an IT employee was $97,430 per year, which is more than double a typical small business employee. So when I add people in, having them at this high rate, that’s dragging down on my overall ability to have a profit for myself because that is just a hit to the bottom line.
And that creates this dynamic where as a company, I either try to hire new people that are beginning of career people and train them up, but as soon as they’re actually good at their job, they’ll be hired by somebody else or I’ll pay them at this higher salary. And if I continue to invest and pay at that, but maybe my competitors that I’m going up against aren’t paying, aren’t investing as much in IT, now my cost to create my goods or products is higher than theirs. So I’m not as competitive as I was if I invest the rate that I need to do so to be compliant and actual secure inside of my environment. So what this has led to is a cloud-enabled outsourcing of my technical talent, meaning my options were either to continue to throw money at this problem or I could just start outsourcing everything.
I can move to cloud products such as Microsoft or the Microsoft 365 lines of services, get rid of the exchange servers in my stack or any of those type of servers. I can have used things like managed service providers, MSPs, where I bring them in to handle my IT. Really just kind of outsourcing all of my technical capability instead of developing that and having the knowledge internally to know what actually is cybersecurity or what actually is proper IT practices. I just want to outsource all that through this process, just moving to the cloud, adopting the cloud and external service providers. And what this creates is through these three main pieces that happened, is a market phenomenon known as the market of lemons. So yeah, Cole, if you want to give us a little bit of a background on what the market of lemons is.
Cole French:
Yeah, absolutely. So like you said, Andy, what you just described does create the conditions for the market phenomenon, called a market for lemons. And I’ll bet most of our listeners out there have probably heard of a product being referred to as a lemon, but maybe aren’t quite sure where that originated or where that came from. Well, maybe actually some of our listeners are aware because typically we refer to a bad car as a lemon, and that is actually exactly where that phenomenon originated back in the 1970s. It was first explored in the used car market by an American economist named George Akerlof. And the core problem in a market for lemons phenomena or market dynamic is there’s an asymmetry of information between sellers and buyers. So quite simply, in the case of a market for lemons, the asymmetry is that sellers hold more information than buyers.
So this makes it difficult for buyers to distinguish between something that’s high quality and something that’s low quality because they don’t have the same level of information as the seller does. And when it comes to used cars, just think of things like CARFAX, I can go to CARFAX and pull up a report on that particular used car and I can see all kinds of information about it. I can see if it’s been in an accident, what the repair history is. I can see a lot of stuff about used cars much more so than I could in the 1970s when George Akerlof was discussing this or coining this and discovering this particular phenomenon. So anyway, back to the asymmetry of information. So that asymmetry means it’s hard for me as the customer to determine what’s high quality and what’s low quality.
But as a customer, as a buyer, I’m still very price sensitive. So I’m only going to pay a certain price for a car or for a service in this case. So we’re obviously taking this market for lemons concept that applied to used cars and we’re applying it to IT services. So as a buyer, I’m only going to pay a certain price. So what ends up happening in a market for lemons is that because I’m only going to pay that certain price, the price in the market actually ends up becoming the average of the high quality and low quality products added together. So that distorts the price and puts sellers in a position that they only sell when they hold low quality products. So because the high quality products are being sold at a lower price, they go quickly, then the market is only left with lemons.
So to summarize the market for lemons phenomenon, so we have asymmetry of information, sellers hold more information. There’s a perverse incentive, so we’re passing off low quality products as high quality products. There is a lack of a credible discourse technology. So again, I mentioned CARFAX a minute ago, so there’s no way for the seller to prove that it’s a quality item, and there’s no way for me as a buyer to definitively say, yes, this is a quality item. There is a wide range of seller qualities. So this drives the average seller quality lower and lower. We’re going to talk about this as it relates to IT services. And really when we get into cybersecurity in particular, the cybersecurity is really where that asymmetry of information in the IT services market is very prevalent. So you’ll see we’ll go into how the wide range of seller qualities actually has a tendency to drive quality low because it has a tendency to drive prices lower and lower.
And then finally, there’s a lack of effective public quality assurance. So there aren’t any warranties or regulations. This is especially true in IT services. It’s kind of the Wild Wild West. And we’re going to talk in particular about how CMMC and the CMMC ecosystem. It provides some hope, I think, in that regard, in that it creates this ecosystem where there is a level of assurance across all the participants in the ecosystem that they’ve been trained, that they’ve gone through background checks, that all these other things that they have certain qualifications to be participating in this market, and hopefully that will bring quality a bit higher. So Andy, now that we’ve talked about and kind of outlined that market for lemons phenomenon, and as I sort of hinted at, we’re going to talk about how this really plays out in the IT services market in general and the cybersecurity services market in particular. So can you just go into how this plays out? Walk us through an example in the IT services market and using cybersecurity services as a really specific example?
Andy Paul:
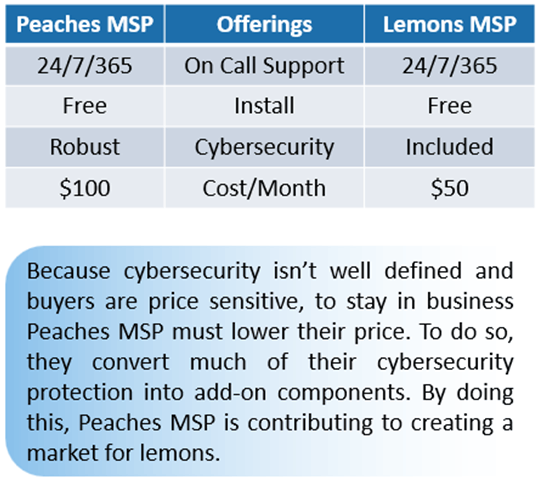
Yeah, sure. So one of the ways that we can really see this happening is you just take two hypothetical managed service providers. We talk about managed service provider. It’s my cousin down the street that’s managing the IT for my company that typically it’s actually an IT firm that we’re going to outsource all this to. So let’s pretend we have two of them inside of our town that we’re in. We’ll call one of them Peaches MSP and the other one Lemons MSP. When me as a business owner that has gone through this process of outsourcing all my technical sophistication through adoption of the cloud, I don’t really have a CIO or a person on staff that is well versed in how to evaluate IT products, and I know I’ve got to keep the lights on, right? I’ve got to have an IT service provider in my organization. I’ll go out and start soliciting quotes from people.
And so we’ve got Peaches MSP and Lemons MSP that I’m going to evaluate. I receive quotes from Peaches MSP comes in, it’s going to be $100 a month, whereas Lemons MSP is going to be $50 a month. I’m like, “Okay.” So evaluate the two of these. So I look at the support that I’m getting. Both are going on for me 24/7 by 365 days, full 24/7 support. Great, that’s the same across. How about installation of their services? They both include that in their price. That’s exactly equivalent. Now, look at the cybersecurity offerings that are being provided. And the Lemons MSP, they include cybersecurity, whereas Peaches MSP provides what they call a robust cybersecurity package. But when I look at that, even if they give me the detailed list of all the things, the technical things that are doing as part of that, I don’t have the technical sophistication to actually tell is that actually needed? Are they selling me smoke? Is that something that actually has a meaningful impact? Am I buying down some sort of risk? Do I even know what that means to buy down risk through cybersecurity investment?
So I don’t understand what’s going on there. But again, because of this information asymmetry, I can’t really evaluate the difference across that line item and I’m cost sensitive, I want to tend to go toward the cheaper provider, because I understand that one of them cost half as much as the other one. So we look back at kind of those five pieces, that information asymmetry. As an average buyer that as a company, I’ve outsourced my technical sophistication to be able to evaluate these two. I can’t tell Peaches MSP can try to tell me that there’s a difference. I’m not even capable of really understanding what those words mean that they’re bringing up. So that definitely hits that information asymmetry piece.
The price incentive obviously is because Lemons MSP, if they’re coming at half the cost, that’s a strong reason for the buyer to go with them. They’re going to grab a higher market share simply because they’re at that lower price. Going into the no credible disclosure, there really isn’t a nationally known or reliable third-party evaluation. There’s tons of them that are out there. Some of them are pay to play with these online review magazines and stuff like that, that really, if you just pay them a little bit extra money, you’ll get a better review. There’s not really a credible way of going out there. Kind of compare that with a lack of public assurance.
IT services does not have a building codes equivalent organization. If I wanted to go install a toilet in your house, I’ve got to be licensed to do that, but I don’t have to be licensed to provide IT services for your bank. I can just go in there and convince them that I’m able to do so and I can contract in order to do that. And then of course, there’s a wide range of quality. We’ve seen this throughout the IT space. You have people at the beginning of their careers versus people at the end of their careers, people that have had experience, been through some of the stuff, actually helped businesses recover from incidents and know why these things are told to be put in there. And you can’t really evaluate that if you’re not from that space.
What happens in this market is that Peaches MSP, in order to stay competitive, has to pull their robust cybersecurity offering out. So they can’t be competitive including that because their customers don’t understand what it means. So they’ll carve that piece out. They’ll put it as add-ons. You can see this today with Microsoft. When you go buy a Microsoft Business Basic $8 a month license, and then there’s all this stuff that I can add on to it, they did that to be competitive with all the other providers that are out there. They absolutely could just include everything. But then that drives it up. So some of those more like $50 a month price ranges where people wouldn’t buy that service as often. So this is the market adapting to this. In order for our customers that are only evaluating on price, I had to pull cybersecurity out of my service offerings, which literally leads back to that concept of the market of lemons has caused this dynamic where the wide range of quality and the price ascendance led to cybersecurity being sacrificed in order for businesses to continue to prosper.
And there’s really not a way for the market itself to necessarily address this, which is one of the big reasons why things like the Cybersecurity Maturity Model Certification seems to be for high sensitive areas is very impactful. So what we do inside of something like CMMC is it’s trying to address that no credible disclosure and a lack of public assurance is attacking those concepts. No different than how CARFAX came into existence to address that market, that piece that was missing on the market that led to the dynamic we’re now seeing that being done by the CMMC. Oh, so and inside of that... Well, actually, Cole, do you want to give us a little bit of a breakdown on how the CMMC ecosystem is helping address that?
Cole French:
Yeah, Andy, I’d be happy to talk about the CMMC ecosystem and how I do believe, I don’t know if this was intentional or not. Certainly, I don’t think they thought, “Oh, there’s a market for lemons in cybersecurity, so let’s set up this CMMC ecosystem.” But that being said, it definitely is something we can hold up as an example of how to solve a problem like the market for lemons. Now, obviously, CMMC ecosystem is relatively new. We got a lot of ground to cover and we’ll see how successful it is in alleviating this market for lemons that we’ve seen with cybersecurity in particular throughout the IT service provider industry. So how does the CMMC ecosystem work?
So the CMMC ecosystem really goes all the way from those who can provide training on the particulars and specifics of the CMMC framework to those that are practitioners of the CMMC framework. So to start, we have licensed training providers, licensed training instructors. These are organizations and individuals that are trained in the CMMC framework and materials, and then they can actually go out and once they are licensed, they can go out and perform that training to the practitioners, which are at least in this case, as of right now, just the assessor side are the only ones that are required to go through a licensed training provider. But once the assessors take the proper courses from the licensed training providers and pass the exam, then they are certified assessors and can perform assessments. Now of course, we’re kind of this still in this rulemaking limbo phase, but this is talking about the framework and the ecosystem kind of as it will function once we’re fully operational sometime early next year.
But then there’s also the consulting side, and this kind of gets into I think our IT services. And Andy’s going to talk a little bit more about what we call the Registered Practitioner side of the ecosystem work. So just to give a primer for that, so there is a designation within the ecosystem called Registered Provider Organization or RPO, and Registered Practitioner. So the Registered Provider Organization is an organizational designation that essentially says this organization is vetted and can perform consulting services on behalf of the CMMC ecosystem. So if I’m company X and I’m out looking for someone to help me get ready for CMMC, I can go to the CMMC marketplace on the Cyber AB website, which we’ll link to in the show notes, and I can look at here’s all the Registered Provider Organizations. So I have a vetted list of organizations I can reach out to and have conversations with about getting ready for CMMC.
And then also, there are Registered Practitioners, which are individuals that have gone through the training, the Registered Provider training, Registered Practitioner training, and have gone through a background check, things like that. So those are individuals that I can also say are vetted and I have some level of trust, that disclosure technology we talked about before with the market for lemons. I can trust that these people do have some level of qualification. That doesn’t mean you shouldn’t have, and we’ll talk a little bit more about this at the end, that doesn’t mean you shouldn’t talk with these folks and have conversations with them and get a gauge on just how knowledgeable they are that the ecosystem isn’t perfect and isn’t going to provide the same level of assurance for every organization. So with that being said, Andy, do you want talk a little bit about Registered Provider Organizations and Registered Practitioners and kind of the value that they bring to the CMMC ecosystem?
Andy Paul:
Yeah, absolutely. So one thing, the way I like to look at it is, so we had this problem. We had this lack of public assurance, and that also went back to the federal government or Department of Defense trying to buy services from companies. There was no way to actually determine if they were there. So they said, “Hey, we’re going to put this in. You got to be third-party assessed.” The ecosystem wouldn’t be able to support that by itself. These companies aren’t able to get through it. They’ve outsourced their technical capability. An RPO fills that gap. It provides a portion of the ecosystem that allows a company to go out and bring in somebody that can operate on their behalf. So when you contract with an RPO, this is the person that brings in that expertise or that knowledge to be able to do several things that otherwise you wouldn’t be able to do.
First, having the knowledge to be evaluate your external service providers, to evaluate products. Is that product duplicative with something I already have? Is that some sort of smoke thing that’s being sold to me? Just marketing terms? Is it actually something that’s meaningful? Does it hit a control that I have to be able to do? Provides them with the ability to scope or design how it is that they’re going to handle a lot of the workflows and the types of information they need to have. It also brings them to somebody that can be a representative on their site. One of the things that’s important when you’re talking about RPOs, it’s the only person in this whole entire ecosystem that’s on the side of your business.
Everybody else is either from the side of the DoD, who’s the person trying to buy services from you. An RPO exists to be on your team, right? They’re helping defend your team from or through the assessment. They’re carrying you through that. They’re providing you with the knowledge to navigate some of those procurement complexities that come up. How to select C3PAOs. So that RPO fits the bill for the missing technical sophistication that was outsourced when we went to the cloud while the C3PAO fits the bill for removing that lack of public assurance that was in there from the market, created by the market of lemons.
Cole French:
Thank you, Andy. That’s a great summary of the RPO and RP construct within the ecosystem. So just to kind of add a little bit more around third-party assessments. I know Andy, your sort of expertise is on the technical implementation, technical solutions side. So the RP, RPO world is definitely an area that you can speak with a lot of expertise to. And then on the Kratos side of things, third-party assessments are where it’s at for us and where our expertise lies. So the third-party assessments, just like Andy mentioned, this is your disclosure technology, and this is getting to if you’re a customer, so on the government side in particular, those assessments provide an assurance that this particular organization and/or the product that they’re leveraging in delivering their service has gone through a third-party assessment and has been certified. So that provides that level of assurance that that organization can handle security.
Now, obviously, this is related to CUI specifically when we’re talking about CMMC, but I think the general framework and the general idea of the CMMC ecosystem is something that we could replicate in, I think, other areas and within the IT services market in some way, shape, or form. What that looks like, how that would manifest and all of that, that’s a difficult thing because there’s not a lot of clamoring for that type of regulation or disclosure technology within the IT services market. It tends to be a niche thing and it has to be driven by government in many cases. So it’ll be interesting to see how this all plays out more broadly. I think it’ll also be interesting to see from a CMMC perspective, how successful will this be? I do know I heard a recent example in which an RPO did not provide quality services, and I think the way that that situation is going to be handled, which is that there’s going to be conversations about the services that were provided.
I don’t know if there’s going to be some sort of repercussion for that organization or how all that’s going to turn out, but I think that’s the idea. Even though the organization that got those poor services still got poor services and kind of has to grapple with the fact that they invested money and time and didn’t get what they were looking for. So that’s obviously frustrating. But there is this third-party ecosystem disclosure, technology warranty, public guarantee type of environment where now there is at least something where that organization that received poor services can go to the Cyber AB and there can be conversations about, okay, what happened here? How can we handle this? How can we ensure that something like this doesn’t happen in the future?
I think that’s kind what we’re getting at and driving quality within the cybersecurity services market. Obviously, this is specific to CMMC, but if we take a step back, back into the sort of outsourcing IT, where we started this conversation, as we bring it to a close here, Andy, if you could give our listeners some good tips on successfully outsourcing CMMC compliance. And I think a key thing to mention here is obviously, this is going to be in a CMMC context again, but really this applies to any kind of outsourcing of IT. I think you can strip out the CMMC parts of it and just say, “Okay, this is from an IT perspective.” And fit that into how your business functions. So Andy, if you want to jump on that, that’d be great.
Andy Paul:
Yeah, absolutely. One of the things that we’ll hear is I contracted with a managed service or I’ve outsourced my IT. So I’ve removed my risk of not passing an assessment. I’ve outsourced my IT to them. They’re going to handle it no different than how I hired a CPA and that CPA is going to defend me through an IRS assessment. That dynamic doesn’t necessarily apply to the MSP. When you contract with your MSP, you as a company are still the one that’s responsible. You contracted with the federal government. You attested when you signed your contract that you’re going to protect their information correctly or any customer. It doesn’t have to be the federal government. You are the one that’s actually responsible for making certain that you’re meeting all these requirements. The MSP gets brought into scope and the new proposed rule that came out did change a couple of things around how being more clear about the managed service providers or any external service provider to your organization being brought in scope.
So one of the big things we want to do is make certain that when we’re evaluating our managed service providers, that using somebody like an RPO that knows how to actually tell what they’re providing. If they give you a letter that says, “Hey, I’m SOC 2 certified.”, does that count? Does that actually meet what we need in order to meet our other stuff? Is that enough? It could be for some companies, in some industries, not in others. That ability to have somebody that’s on your side for evaluating your outsourced IT really helps. It’s also really important to evaluate your IT providers by looking at their past success. In CMMC, do they have customers that they’ve taken through? Have they achieved it themselves? Really as one of the big pieces. You’re not going to be able to necessarily quiz them because again, you’ve outsourced your IT specification.
You’re not going to be able to quiz them or find trip up questions. So really looking at that kind of past performance is one of the real big ways to be able to evaluate that. And then of course, going to the ecosystems, seeing what they’ve done in the way of third-party assessments. So for instance, in the CMMC space, making certain that they’re listed, the person assigned to your account is listed there as at least an RP, but trying to preference higher up things like the CCPs or the CCA designations, making certain that the organization itself is actually certified by the accreditation body to make sure that they can provide those services. And then we want to look out for, there are some red flags, some things that are out there that can really jump out at you as items that should scare you away, things that can jump up for it.
Cole, I don’t know about you. I know for myself, one of the things that I always look out for is if, especially within the CMMC context, is that can they give me an actual responsibility matrix? A lot of times, an MSP that has been through this, that is ready to go and they just can hand that to you the second that you ask for it, whereas if they can’t rapidly provide that, they probably haven’t been through it themselves yet. Cole, how about you? Have you seen any other major red flags to watch out for?
Cole French:
Yeah, absolutely. I kind of break them down on managed service providers and external service providers as well. I think some people are like, “Well, aren’t those the same thing?” But I think they’re a little bit different. A managed service provider typically is somebody who’s actually performing a service on my behalf. Then there’s external service providers, which is I am leveraging something that this organization is providing, but I’m actually the one using it, managing it, et cetera. So on the managed services side, I would agree with Andy, that that responsibility matrix... In a shared responsibility matrix, for those of you don’t know, that’s the managed service provider actually can tell me what their level of responsibility is for implementing controls. It doesn’t necessarily have to be CMMC. It could be another framework of controls, could be 853, but something that I can use to map back to CMMC or NIST 800-171 controls. Right off the bat, that’s the first thing Andy mentioned. Got to have that. If you don’t have that, that’s a non-starter.
The MSP should also be able to share information with you. What kind of baseline configurations do they use? Do you have input in those baseline configurations of the systems that they’re managing on your behalf? What kind of tool sets do they use? Do they use the same tool sets for CMMC clients and non-CMMC clients? As I’ll get into with external service providers, there’s some trickiness around like FedRAMP authorized systems and things like that. Is the MSP willing to participate in an assessment? So if I’m leveraging an MSP and I’m about to go through a CMMC assessment, or frankly, an assessment against any framework, and my MSP is like, “No, we’re not going to participate. We’re not going to help out with that assessment. That’s not part of our service level agreement with you.”, that’s a major red flag. You want to have the MSP as embedded in your organization as much as possible so that way, they can come online and they can come and support these assessments that you’re going to go through just like they were part of your organization.
And then finally, if an MSP, and Andy, you mentioned this SOC 2 other, there’s other frameworks out there, if an MSP points to that and says, “That makes us compliant.”, don’t take that as gospel. Don’t take that as truth. There’s nuance there. Not every framework or certification, particularly SOC 2, which you hear that a lot, SOC 2 is a very kind of niche certification and definitely is not applicable to a lot of these other frameworks. So be aware of those who want to throw acronyms out there and say that that covers them from a security perspective. So that covers our managed service providers. And switching over to external service providers, really the biggest thing with external service providers is FedRAMP equivalency, which used to just be FedRAMP moderate, right? The DFARS said FedRAMP moderate or equivalent.
But that has since been clarified in the memo, the equivalency memo, FedRAMP equivalency memo that was released earlier this year, which basically says FedRAMP moderate authorized or higher or a FedRAMP equivalency assessment is performed. So any external service provider you’re looking to leverage or external service really, because that could be a SaaS product as well, which is not really provided by a provider, but it is a product that you leverage that can be FedRAMP authorized or not make sure that you’re leveraging FedRAMP authorized service offerings or cloud service offerings or cloud service products. And then also beware with external service providers, their use of US versus non-US persons. That could become challenging in certain contexts within CMMC. And certainly when you get into ITAR and other things like that, that is definitely something to know and understand upfront because that is something that could become problematic later on.
And then again, I would say if you’re looking at it from a CMMC perspective and you’re using external service provider and they can’t really provide you with any information on how they meet NIST 800-171 controls or really whatever framework you’re working with, if they can’t tell you, “Hey, this is how we’re meeting the specific controls of that framework.”, that’s definitely a red flag. I wouldn’t say that’s a non-starter, but definitely something that should give you pause and you should request that they pull something like that together and provide that kind of information. So we’ll drop those in the show notes as well so that you guys can check those out, refer to them as you’re going about your journey.
So as we wrap up this conversation today, Andy, we’ve talked about the market for lemons, we’ve gone through the CMMC ecosystem, we’ve talked about IT service providers, and we’ve just gone over some of those red flags. But some people out there may be wondering, well, how do I know if I’m successfully outsourcing my CMMC compliance in particular? So to close this out, could you just kind of go over what are some of the things folks should be looking for to successfully outsource CMMC compliance?
Andy Paul:
Yeah, absolutely. So when you’re trying to outsource your CMMC compliance, a couple of things to make certain that you’re focusing on, you want to spend some time understanding how control inheritance works. So we talk about control inheritance and saying this other... I bought something I don’t have to worry about that now. A good example of that is I’m storing my data in a Microsoft cloud, I don’t have to worry about how we control access to the physical server that it’s on. You can’t modify that. Microsoft handles it as control of inheritance. However, just because you inherit that control, does not necessarily mean you have no responsibility in it. So this is one of those things that an RPO can help walk you through. Or if you’re just trying to buy some of those external service providers, make certain that you understand that you still have responsibility, you have these configured products, you have to make certain that you use them correctly and as intended.
So really spend that time developing my control inheritance for all the products that I’m leveraging. Don’t underestimate the concept of the shared responsibility matrix. Make sure we’re focusing on that for any external service provider. Exactly what’s their scope, what’s in your scope? What are the things that you’re going to be expected to do? The assessor, especially for CMMC, is going to get into that level. And if you are not ready to speak to this was why it was outsourced, this is my responsibility, that’s what presents you problems when you go through your assessment. It’s also important to look up and spend a little bit of time understanding reciprocity. Talking about things like SOC 2. SOC 2 does not have reciprocity inside the CMMC assessment. Just because somebody has that, they might as well not when it comes to CMMC. There’s only FedRAMP and CMMC certifications that have reciprocity there.
So don’t rely on something, thinking that you can trust that certification as something that you can leverage as part of your overall strategy to achieve CMMC. Another thing that we see a lot is an oversimplification of the administration or administrative documentation requirements. This is the SSP, but will detail you write your SSP to the other plans, policies, and procedures. Relying on templates to build this out is typically a quick path to failure. What I mean is there’ll be stuff written in there that you just kind of include because it’s bullet proof language, it sounds good, but if you write it in your plans, you write it in your policy, you have to do it. And an over-reliance on templates without actually going through and spending the time to customize them to your organization and make sure that you can and do perform all the activities that are in there is one of the problems that people run into. So don’t overrely on those. Even if you try to use template sets, know that you still have to spend the time going through and customizing those fully to your organization.
And finally, as you’re preparing to outsource CMMC, focus on evidence, right? There’s always more than one type of evidence we needed for every control. So make certain that you have a whole bunch of evidence. You have to be able to demonstrate both adequacy and sufficiency. I’m not going to go into what that means here today, and that is one of the reasons why we strongly suggest if you’re not working with an RPO, to go ahead and bring one of those in to help you understand, is this enough evidence to prove both adequacy and sufficiency of the control is met?
But there is going to be a lot of evidence. You have to be able to prove all these things that you’re saying that you’re doing within your policies, within your SSP. So keeping all those five points in mind, what will help you be able to successfully outsource your CMMC compliance and make certain that you’re not creating weaknesses in your supply chain, you’re also not oversimplifying something. Because what we don’t want you to do is go spend a year getting ready and then have something that creates a problem where you’re not even going to pass readiness for your assessment.
Cole French:
Yeah, that’s a great list, Andy. And just like the list of red flags, we’ll definitely drop that list in the show notes and provide some context and explanation like Andy just went over. Just give you guys something to refer back to when you’re having these conversations. And as we wrap up, I just want to mention too, that trust your judgment. As you’re going through this and you’re talking to Registered Provider Organizations or Registered Practitioners. Just keep in mind, I think sometimes we do, I know we talked about this market for lemons and the complicated nature of what exactly am I getting? I think that’s hard when my business is to build a particular product, I’m not really in IT or cybersecurity, it can be hard to understand and discern what I’m actually getting. But you can always rely on and go back to if somebody’s promising me a whole bunch of stuff and it’s not going to cost me that much money, kind of goes back to that whole too good to be true thing.
So I just want to put that as a reminder as we close that I do think just using that sort of gut feeling judgment is helpful here. And then leverage that ecosystem. If you talk to one provider and what you get from them is like, “Man, that sounds like they’re selling me the world for not that much money.”, go talk to another provider, talk to multiple providers, get multiple perspectives. That’ll help you really understand what you’re getting and what you’re not getting. So with that, Andy, thank you again. Always a pleasure to talk to you. Appreciate you coming on and sharing your perspective today on the Cyber Compliance and Beyond podcast.
Andy Paul:
Thank you.
